How the Internet Works: Features and Protocols
| ✓ Paper Type: Free Assignment | ✓ Study Level: University / Undergraduate |
| ✓ Wordcount: 4151 words | ✓ Published: 06 Jun 2019 |
Contents
Task 1: What is the internet?
The internet is a global Wide Area Network, connecting millions of machines together. It is used to share information along with many other things and is used more and more as we progress into the future. We connect to the internet through Inter Service Providers and are each a host to a world-wide network.
How do we connect to the internet?
Once you have purchased an Internet Services, the Internet Service Provider should send you a router. The router, once set up will provide you a connection to the internet. So, what is the process?
Firstly, the router has 2 IP‘s. One, is public, which is used externally, to connect with the ISP. The second one, is for internal use, for your personal area network. You may connect to the router by an ethernet cable or wi-fi. The router gets its connection from the Internet Service Provider. The ISP‘s use internet exchange point to exchange their internet traffic, it is used to facilitate network interconnection through an exchange point, instead of third-party networks.
The Internet exchange point then connects to the Backbone. The backbone is a high-speed data transmission line, that provides networking facilities to internet service providers. The Backbone is controlled by Cisco, who is responsible for the global network infrastructure.
What is DNS?
The Domain Name System (DNS) enables you to find web sites by the human-readable hostnames. The DNS system allows the machine-readable addresses to be found by human-readable names, which contain letters, machines mainly use numbers. The DNS is like a phone book for the internet. If you want to know what is John Johnsons phone number, you look it up in the book. Same for the internet but just different content. Without this system, you would have to manually insert the website IP address to access it. There is a number of steps in how a DNS works, how it transfers information between human and machine-readable addresses.
Step 1: Requesting information
When you enter a search name in your web browser, let’s say “central college”, first thing the computer does is look into its local DNS cache, which stores information that your computer has recently retrieved. If there is nothing relevant, the computer performs a DNS query in order to find out.
Step 2: Ask the recursive DNS servers
If the information isn’t found locally, the computer contacts the ISP’s recursive DNS servers. These specialised computers do the work for your DNS query. Recursive servers have their own caches, so the process most often ends here and the information is returned to the users.
Step 3: Ask the root nameservers
If the recursive servers failed to provide an answer, they contact the root nameservers. These nameservers answers questions about the domain names, such as IP addresses. The root nameservers act as a switchboard for DNS. They don’t know the answer but they do know who to redirect you to.
Step 4: Ask the TLD nameservers
Top Level Domain nameservers. The root nameservers read the addresses from right to left. www.centralcollege.com. And then direct the query to the TLD nameservers. For .com. These servers don’t know the answer, but they direct you to the servers that do have the information.
Step 5: Ask the authoritative DNS servers
The TLD nameservers then review the next part of the request – the one between www. And .com. Then direct our queries to the nameservers that are responsible for the specific domain. These authoritative nameservers are responsible for knowing all of the information on a specific domain, which is stored in DNS records. There are many types of records which each contain different, specific information. In this case, we want to know the IP address, so we ask the nameserver for the address record (A).
Step 6: Retrieve the record
The recursive server retrieves the A record for www.centralcollege.com from the authoritative name servers and stores the record in its local cache. If anyone tries looking up the host record for the website again, the recursive servers already have the needed information and will not need to go through the process again.
All records have a TTL(time to live) value, an expiration date in other words. At some point, the recursive servers will need to ask for a new copy of the record to make sure everything is up-to date.
Step 7: Receive the answer
Once equipped with answers, the recursive server returns the records to your computer, which stores the record in its local cache. The computer reads the IP address from the record and then establishes a connection with the webserver and receives the website.
The whole process only takes milliseconds to complete.
What is TCP/IP?
Transmission Control Protocol/Internet Protocol, is a set of communication rules used to interconnect network devices on the internet. The TCP/IP can also be used as communications in private networks like intranet or extranet. The TCP/IP states how data is exchanged on the internet, by providing end-to-end communications that state how something should be broken down in packets, addressed, transmitted, routed and received at the destination. These protocols are designed to make networks reliable and are given the ability to recover automatically after a failure of any device or network. Both TCP and IP serve specific functions. TCP defines how applications can create channels and communicate across the network. It also organised how a message is broken down into smaller packets before being transmitted over the internet and then brought back into one message at the destination address.
IP defines how to route and address each packet to make sure it reaches its destination. Each gateway computer on the network checks the message’s IP address to find out where to forward the message to. The TCP/IP uses a client/server model of communication in which a user or machine (the client) is provided a service like sending a web page, by another computer (server) in the network. TCP/IP set of protocols is classified as stateless, which means every client request is considered as new because it is unrelated to previous requests. Because it is stateless, that means there are more free network paths, therefore, they can be used continuously. However, in the TCP/IP model, the transport level itself is stateful. This means it transmits a single message and its connection remains in place until all packets in the message have been received and reassembled at the destination.
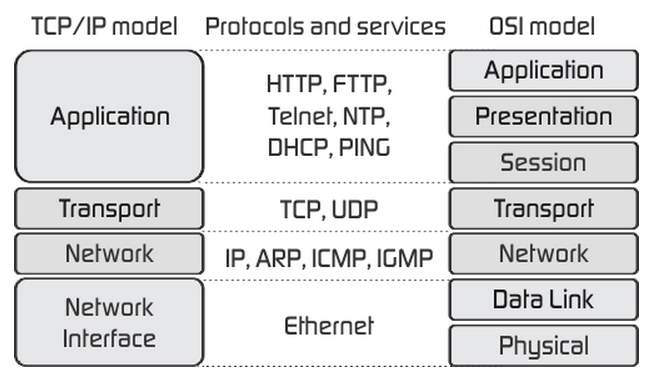
The TCP/IP Model layer
The application layer
The Application layer provides applications with standardised data exchange. The protocols used are: Hypertext transfer protocol (HTTP), File transfer protocol (FTP), post office protocol 3 (POP3), Simple mail transfer protocol (STMP) and simple network management protocol (SNMP).
The Transport layer
This layer is responsible for maintaining end-to-end communications across the network. The TCP is responsible for communications between hosts and provides flow control, multiplexing and reliability. Transport protocols are: TCP and User Datagram Protocol (UDP), the UDP is sometimes used instead of TCP for specific purposes.
The network layer
Also called the Internet layer. This layer deals with packets and connects independent networks to transport the packets across the network boundaries. Network layer protocols are the IP and the Internet Control Message Protocol (ICMP), which is used to report errors.
The Physical layer
This layer includes protocols that operate only on a link – the network component that interconnects networks nodes/hosts in the network. The protocols in this layer include ethernet for LAN’s (Local Area Network) and Address Resolution Protocol (ARP).
- Your browser connects to the web server, requesting a web page;
- A machine running the web server;
- Your computer running a web browser.

The web server then sends the requested web pages back to your computer
What is an IP address?
Internet Protocol Address. An IP address is a numeric address assigned to every computer, phone, switch, router etc., that uses the TCP/IP based network. IP address is the core on which the networking architecture is built. Every node in a network must have it, otherwise it would not exist. An IP address is logical; therefore, it can change.
They are uniquely used to identify every single node in a network. As an example, let’s take Nottingham. Every street, house and building have a name and number, so it can be found and because of that communication is possible. The numbers in an IP address is split into two parts: The network part, which specifies which network the address belongs to, and the part which specifically states the location.
The IP addresses bind the WWW (World Wide Web) together. As I mentioned, every node in a network must have an IP address. It is the most significant and most important component in networking. IP address is key to networks that use TCP/IP communication protocols. Nodes in the network are assigned IP addresses by the DHCP (Dynamic Host Configuration Protocol) server as soon as the node connects to the network.
The DHCP assigns IP addresses using the pool of available IP addresses. The DHCP is only used to provide dynamic IP addresses, whereas a static IP is assigned to a machine forever and cannot be used again.
Static and Dynamic IP addresses
A static IP address remains the same, when you start up your computer, connect to the network, you are always connection through the same IP. There are several advantages of a static IP: It is more reliable for VoIP and gaming applications and if you want to use your PC as a server, a static IP would provide faster download and upload speed. Disadvantages of a static IP: Because your public IP does not change, it makes it easier to trace your internet activity back to your IP and it is costlier compared to the dynamic IP address.
A dynamic IP constantly changes. This means that every time you log onto the network, you will be issued a different IP address. Some advantages of a dynamic IP address: It is cheaper than static IP’s and it can grant you more privacy. Some disadvantages: You need to check your IP, given that it is always changing. A DHCP server is required to obtain your IP address.
What is a web server?
A web server is a program that uses Hypertext Transfer Protocol (HTTP), to serve the files that form web pages to users after their HTTP clients have requested the pages. Dedicated computers and appliances are called web servers as well. All computers that are hosting web sites must have a web server program.
One of the most widely popular web server would be Apache. Web servers are often used for serving email, downloading requests for File Transfer Protocol (FTP) files as well as building and publishing web pages. A When choosing a web server, the following should be considered: How well it works with the operating system, other servers, its ability to handle server-side programming, security, publishing search engine and site building tools that come with it.
Task 2: DDoS
DDOS stands for Distributed Denial of Service. A DDoS attack is used to slow down or completely deny service to a network or a website. A DDoS attack is achieved via botnets. A DOS attack is used when attacking a network or a system from only one computer. The aim of such attacks is to put a network or a website under such pressure that it cannot deal with it therefore is hugely slowed in service or completely denied of it. The impacts of DDoS is not data theft or loss of information, but to, as the name suggests, deny the access to service.
This can still be just as effective because if an online company gets DDoS’ed, the customer might choose to switch providers because simply not affording to wait for the companies’ websites to come back up. There isn’t a way to completely prevent DDoS, but it is possible to make it much harder to DDoS you. Things like server load balancers, anti-DDoS programs or you might contact your ISP provider to reroute your traffic.
XSS
Cross site scripting. XSS is when a trusted website is injected with a malicious code, then the other end-users that download from the trusted website, will also download the malicious code, without the packets being checked as it is downloaded from a trusted web page. The injection is often done by sending untrusted information to the web page. For example, a web request. When the web request is sent, the code is inserted into the website if steps are not taken to prevent cross-site scripting. The effects of XSS often range from data theft, scamming and taking control of user’s session.
Website poisoning
( downloading)
downloading)
Drive-by download attacks is somewhat similar to XSS. A malicious code is embedded in the website, and when a user comes upon the website, the code starts scanning your system for security vulnerabilities. When one is found, the malware goes on to infiltrate your system and takes control of it. This might happen for a few reasons. You are often infiltrated because of outdated apps or chats. Firstly, you might not update your softwares enough or you might have plugins in your browser that you are unaware of.
SQL injection
An SQL injections alters the SQL statements in the web application through the attacker-supplied data. Improper construction of SQL statements or insufficient input can lead to being exposed to suck attacks. An SQL injection can result in data theft, loss of control of the website. SQL injections are rated the number one threat to web applications by OWASP.
Hacking
Computer hackers look for vulnerabilities in the computer code(which makes your computer run) and break in. There are several reasons why a hacker might do so: To cause harm, steal information or simply for fun or practice.
Data theft
Data theft means unauthorised copying or removal of information from other users or businesses. This can range from your confidential information from a nation-wide enterprise to who you text at 9 pm before going to sleep.
Brute force
A brute force attack is a method used for data theft, in more detail to crack passwords. (brute force cracking), In a brute force attack, automated software’s are used to generate large amounts of guesses. Brute force attacks are used by hackers to crack encrypted data or to test the security of an organizations network.
Task 3: The role of web architecture in website communications
In order to communicate with websites, the right web architecture must be in place. Without it, the users will be unable to connect to the internet and web servers would be unable to answer requests. The key architecture used by the web are:
Internet service provider (ISP)
An ISP, as the name suggests, provides you a connection to the internet. An Example of an ISP is BT, Virgin Media. Usually, a monthly payment would have to be issued in order to keep your connection. A router would be sent to you by the ISP in order to connect to the internet.
Web Hosting Services
Web hosting services are provided by companies that are dedicated for hosting websites on their servers. Buying their services would cost, but it would also allow our website to be accessed by everyone on the internet. Different packages exist for the payment, each include different storage amount or expected traffic load that would be handled.
Domain Structure
The web addresses can be broken down into different parts. Let’s take https://www.facebook.com/ as an example. (https://), (www.) and (facebook.com). This allows your web browser to determine what kind of a web site it is. The https protocol tells the browser that there should be a SSL certificate present.
Domain Name Registrars
Domain Name Registrars are companies in charge of selling domain names. These companies are accredited by the Internet Corporation for Assigned names and numbers (ICANN) or a national country code top-level domain. They would sell domains such as “.com” and “.org”.
World Wide Web
The World Wide Web is an information system on the internet that allows files to be connected to other files through hypertext links, allowing users to search for information by moving from one file to another.
TCP/IP Application layer protocols
“The Application layer provides applications with standardised data exchange. The protocols used are: Hypertext transfer protocol (HTTP), File transfer protocol (FTP), post office protocol 3 (POP3), Simple mail transfer protocol (STMP) and simple network management protocol (SNMP).” –Task 1
I will explain what each of the protocols does.
Hypertext transfer protocol (HTTP)
This protocol is the underlying protocol used for the World Wide Web and the protocol defines how messages are formatted and transmitted along with what actions web servers and browsers should take under specific commands. An example would be: When you enter a URL into your web browser, it actually sends an HTTP command to the web server telling it to find and send the requested web page to the browser.
File Transfer Protocol (FTP)
File Transfer Protocol is a commonly used protocol for file exchange over the internet. FTP uses TCP/IP protocols to enable file transfer. It also uses client-server architecture, therefore functions similar to HTTP. FTP promotes sharing files over the internet via remote computers with reliable and efficient data transfer. FTP functions similar to HTTP because it transfers web pages from a server to user’s browser.
Post Office Protocol 3 (POP3)
The Post Office Protocol 3 is used to retrieve e-mails from the mail server. Most e-mail applications use POP3; however some might use the newer protocol, Internet Message Access Protocol (IMAP). There are two versions of POP, POP2 and POP3. POP2 was standard in the mid-80s and required he SMTP o send messages, however POP3 can function with or without SMTP.
Simple Mail Transfer Protocol (SMTP)
This protocol is used to send e-mail messages between servers. Most e-mail systems use SMTP when sending mail over the internet. The e-mails sent can be retrieved by mail clients using POP/IMAP. Furthermore, SMTP is generally used to send mail from the mail client to the mail server that is why you need to specify both POP and IMAP server and the SMTP server when you configure your e-mail client.
Simple Network Management Protocol (SNMP)
SNMP is a commonly used protocol for network management. It is a suite of protocols that are supported by many devices such as routers, servers or printers. Supported devices are all network-attacked and must be monitored to detect conditions. The conditions need to be addressed for proper, ongoing network and appropriate administration.
Short explanation for OSI 7 layer model
Layer 7 – Application
This layer supports application and end-user processes. This is things like e-mails and web browsers.
Layer 6 – Presentation
The presentation level is responsible for organization of data into a format that can be used by humans.
Layer 5 – Session
This layer allows you to have a multiple browsers and resources open simultaneously without data conflicts in transmission.
Layer 4 – Transport
This layer is the firewall layer. Four switches operate at this level.
Layer 3 – Network
Logical address for a server or work station is managed here. Common protocol is TCP/IP. Routing takes place at this level.
Layer 2 – Data link
Physical address, MAC (Media Access Control) used to identify the device. Frame relay is used here.
Layer 1 – Physical
Cables/Wireless. Encoding bits of data.
OSI model and TCP/IP
Comparing the upper layers
OSI, The session layer allows two stations to hold an ongoing communication channel called a session across the network. However, in TCP/IP, this is not found, its characteristics are provided by the TCP protocol, in the transport layer.
The presentation layer is responsible for data format information for networked communications. It is done by converting data into a human-understood format, so that it is more useful for both sides. This is not found in TCP/IP, in TCP/IP, this function is provided by the Application layer.
Application layer is the top layer of the OSI model. It provides a suite of interfaces for applications to get access to networked services as well as access to the network services that support applications directly. Although the notion of an application process is common to both of them, their approach to constructing application entities is different.
Their approach: ISO Approach
In this model, it is sometimes called the Horizontal approach. OSI asserts that distributed applications work over a strict hierarchy of layers and are constructed from a common tool kit of standardised applications. Each distributed application service selects functions from a large common toolkit of application service element (ASEs) and complements these with application service elements that carry out the specific functions for the end-user service.
TCP/IP Approach
It is sometimes called the Vertical approach. In TCP/IP, each application entity is composed of whatever suite of functions it requires beyond end to end transport to support a distributed communications service. Many of these application processes builds on what it requires and assumes only that an underlying transport mechanism (datagram or connection) will be provided.
Transport layer
The functionality of the transport layer is to provide “transparent transfer of data from a source end open system to a destination end open system” (ISO / IEC 7498: 1984).
Transport is responsible for maintaining and creating the basic end-to-end connection between communication open systems, ensuring that the bits delivered to the receiver are the exact same as the bits transmitted by the sender; in the exact same order and without having been modified, duplicated or being lost.
OSI Transport layer
It consumes the information to be sent and breaks it into individual packets that are sent and put back together into a complete message by the Transport layer at the receiving machine. Also, it is the transport layer’s job to provide a signaling service for the remote node so that the sending node is notified when its data is received successfully by the receiving node.
Transport layer protocols include the ability to acknowledge the receipt of a packet; if no acknowledgement is received, the Transport layer protocol can retransmit the packet or time-out the connection and signal an error. Also, transport protocols can mark packets with sequencing information so that the destination machine can properly order the packets if they’re received out-of-sequence. Furthermore, Transport protocols provide facilities for insuring the integrity of packets and requesting retransmission should the packet become stuck when routed.
TCP/IP transport layer
The TCP/IP transport layer defines two standard transport protocols: TCP and UDP, TCP provides a reliable data-stream transmission and UDP is useful in many applications. Main difference between the two, is that UDP does not necessarily provide reliable data-stream transmission. TCP is also responsible for recovering data by providing a sequence of numbers with each packet that it sent, it requires acknowledgement to ensure correct data was recovered. Packets may be retransmitted if errors were detected.
Comparison of both models
UDP and TCP features defined for TCP/IP transport layer corresponds to many of the requirements in the OSI transport layer. However, there is a little bit of a bleed over for requirements in the session layer of OSI because of sequence numbers and port values can help to allow the operating system to keep track of sessions, but many of the TCP and UP functions and specifications from the TCP/IP, map to the OSI transport layer. The TCP/IP and OSI architecture models both employ all connection and connectionless models at transport layer.
However, the internet architecture refers to the two models in TCP/IP by the simple terms “connections” and datagrams. But the OSI reference model, with its liking of the “precise” terminology, uses the terms connection-mode and connection-oriented for the connection model and the term connectionless-mode for the connectionless model.
Bibliography
- Impacts of DDoS, (Accessed October 2017)
- Ways to prevent DDoS, (Accessed October 2017)
- What is Cross-site Scripting, (Accessed October 2017)
- SQL injection, (Accessed October 2017)
- IP address, (Accessed November 2017)
- Static and dynamic IP, (Accessed November 2017)
- TCP/IP, (Accessed November 2017)
- Web servers, (Accessed November 2017)
- Task 3
- HTTP – HyperText Transfer Protocol, (Accessed November 2017)
- FTP Meaning & Definition | What is FTP?, (Accessed November 2017)
- POP3, (Accessed November 2017)
- SMTP, (Accessed November 2017)
- SNMP, (Accessed November 2017)
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this assignment and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal